Explain How Securing Iscsi Differs From Other Protocols
ISCSI does not require dedicated. Mechanisms for storage network security explain threats and their security exposures as well as describe.
Setup Iscsi Target Initiator On Centos 6 Root Opentodo
Protocol to different media carriers such as Fibre Channel or even other transport protocols as TCPIP.
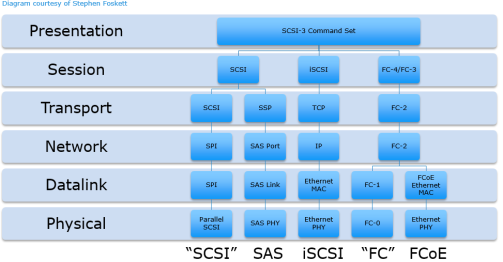
. Of course it is a data sharing network protocol. It enables block-level SCSI data transport between the iSCSI initiator and the storage target over TCPIP networks. It transmits data using the TCPIP protocol over familiar Ethernet networks that are supporting network traffic in data centers right now.
The primary security risk to iSCSI SANs is that an. NFS offers you the option of sharing your files between multiple client machines. In a previous Storage Basics article we looked at securing IP communications using the IPSec protocol.
ISCSI facilitates data transfers over intranets and to manage storage over long distances. SCSI uses a controller to send and receive data and power to SCSI-enabled devices like hard drives and printers. Protect Valuable Data Ÿ Secure IP connection Integrity authentication and confidentiality Based on IKEv1 and ESP IPsec components Ÿ Extensive applied security requirements Selection of Integrity MAC and encryption algorithms Profile for usage of IKEv1 authentication and key management Ÿ Inband authentication part of Login.
ISCSI is very cost efficient and can be easily understood by any IT guy. Unlike most security systems that function within the application layer of the OSI model IPsec functions within the network layer. ISCSI is the SCSI protocol mapped to TCPIP and run over standard Ethernet technologies.
In the SSP market iSCSI enables initiators secure access to centralized storage located at an SSP Internet Data Center IDC by removing the distance limitations of FC. However many people often use the term ICSI or IVF-ICSI to refer to the entire fertility treatment process. Full TCPIP stack versus TCPIP Data Path only offload Several NASs already implemented TOEs.
Security role management and access. SAN Security Protocols and Mechanisms 7 iSCSI enables SCSI-3 commands to be encapsulated in TCPIP packets and delivered. ISCSI supports encrypting the network packets and decrypts upon arrival at the target.
Unlike fiber channel iSCSI doesnt operate over a separate network protocol. Products people and procedures. Intracytoplasmic sperm injection abbreviated as ICSI is one of the steps of in vitro fertilization treatmentSpecifically ICSI refers to the method of fertilizing oocyte with sperm.
ISCSI supports two separate security mechanisms. With many storage implementations moving toward IP-based solutions such as iSCSI the importance of securing IP transmissions becomes critical especially considering that many of the programs we use send clear text across the network. This allows Ethernet networks to be deployed as SANs at a much lower TCO than Fibre Channel FC.
ISCSI is a block protocol for storage networking and runs the very common SCSI storage protocol across a. Internet Small Computer Systems Interface or iSCSI is an Internet Protocol-based storage networking standard for linking data storage facilities. Its been around for more than 20 years and its been thoroughly tested so it has a reputation for being reliable.
Despite the current adoption trend in low-end environments iSCSI is a very robust technology capable of supporting relatively high-performance applications. The task of protecting the integrity confidentiality and availability of information on the devices that store manipulate and transmit the information through products people and procedures. Approaches to securing storage traffic vary with the storage protocols and infrastructures you plan to use.
It can be used to transmit. The SNIA dictionary defines Internet Small Computer Systems Interface iSCSI as a transport protocol that provides for the SCSI protocol to be carried over a TCP -based IP network standardized by the Internet Engineering Task Force and described in RFC 3720. ISCSI on the other hand would support a single for each of the volumes.
Each server and each storage device has its own IP address es and you connect by specifying an IP address where your drive lives. IPsec provides authentication services and encapsulation of data through support of the Internet Key Exchange IKE protocol. Configure iSCSI initiator.
To configure the initiator open the Server manager - Click on tools and click on iSCSI initiator. ISCSI stands for Internet Small Computer Systems Interface. AoE translates the Advanced Technology Attachment ATA storage protocol directly to Ethernet networking rather than building on a high-level protocol as iSCSI does with TCPIP.
ISCSI is a flexible protocol which can work within any environment. ATA over Ethernet AoE is another Ethernet SAN protocol that has been sold commercially mainly by Coraid Inc. It is referred to as Block Server Protocol similar in lines to SMB.
ISCSI is entirely different fundamentally. Here you can specify the IP Address or DNS Name of the iSCSI target server. ISCSI means you map your storage over TCPIP.
In-band authentication between initiator and target at the iSCSI connection level. You typically put in dedicated Ethernet network cards and a separate network switch. For example if you are using Fibre Channel that fibre channel infrastructure is going to be isolated from your Ethernet network thus creating a physical segmentation similar to what you see in the traditional datacenter.
ISCSI is a transport layer protocol that works on top of the Transport Control Protocol TCP. Therefore in this article we are going to detail step by step all the phases of IVF-ICSI. ISCSI provides block-level access to storage devices by carrying SCSI commands over a TCPIP network.
In Windows each drive shows up in Computer Manager as a hard drive and you format it. Whereas FCoE encapsulates native Fibre Channel packets inside of Ethernet packets iSCSI encapsulates native SCSI commands inside of IP packets. Like CHAP authentication occurs during login into storage Packet protection by IPsec at the IP level all packets are secured.
This allows users to have different levels of authorization. Parallel SCSI and serial attached SCSI SAS are technologies designed to be inside a box such as DAS or within a storage array. SCSI has several benefits.
A dialog box to configure it opens. In addition to the administrator role for administering DSM and SCOS there is also a restricted volume manager role that must be granted permission to volumes storage hosts or disk folders. Its fairly fast up to 320 megabytes per second MBps.
Little or no investment in new network technology is. TCPIP or TCPIP and iSCSI offload. One may ask why iSCSI is recommended over other protocols.
Explain physical social engineering attacks.

How Iscsi Compares With Other Storage Transport Protocols Iscsi Implementation Guide For Dell Emc Storage Arrays Running Powermaxos Dell Technologies Info Hub

5 3 Iscsi Architecture And Addressing Mycloudwiki

Iscsi Security Considerations In The Cloud Infosec Resources

Comments
Post a Comment